TL;DR: Proper configuration of SPF, DKIM, DMARC, and BIMI records isn’t just a technical best practice—it’s now a business imperative that directly impacts email deliverability, brand protection, cybersecurity, and regulatory compliance.
In today’s digital landscape, email remains the backbone of business communication, handling everything from customer outreach to financial transactions. Yet despite its ubiquity, email security often receives inadequate attention until it’s too late. Business email compromise attacks accounted for 73% of all reported cyber incidents in 2024, making email authentication no longer optional but essential for business survival.
The stakes have never been higher. Claims severity involving business email compromise (BEC) increased 23% in 2024, with an average claims cost of $35,000, while BEC scams have cost businesses more than $55bn since 2013. These staggering figures underscore a fundamental truth: businesses that fail to implement proper email authentication are not just vulnerable—they’re playing Russian roulette with their reputation and finances.

The Four Pillars of Email Security
SPF (Sender Policy Framework): Your First Line of Defense

How SPF Works
Sender Policy Framework acts as a digital bouncer for your domain, specifying which mail servers are authorized to send emails on your behalf. When an email arrives, the receiving server performs a DNS lookup to check if the sending IP address is listed in the domain’s SPF record.
Sender Policy Framework acts as a digital bouncer for your domain, specifying which mail servers are authorized to send emails on your behalf. When an email arrives, the receiving server performs a DNS lookup to check if the sending IP address is listed in the domain’s SPF record.
Technical Process
- Receiving server extracts the domain from the email’s “Return-Path” header
- Performs DNS TXT record lookup for the domain
- Compares sending IP against authorized IPs in SPF record
- Returns Pass, Fail, Soft Fail, or Neutral result
Sample SPF DNS Record
yourdomain.com TXT “v=spf1 include:_spf.google.com include:sendgrid.net ip4:192.168.1.100 -all”
Record Breakdown
- v=spf1 – SPF version identifier
- include:_spf.google.com – Authorize Google Workspace servers
- include:sendgrid.net – Authorize SendGrid servers
- ip4:192.168.1.100 – Authorize specific IP address
- -all – Reject all other sources (hard fail)
Current Adoption Statistics
SPF Adoption by Domain Rank (Top 1M Domains)
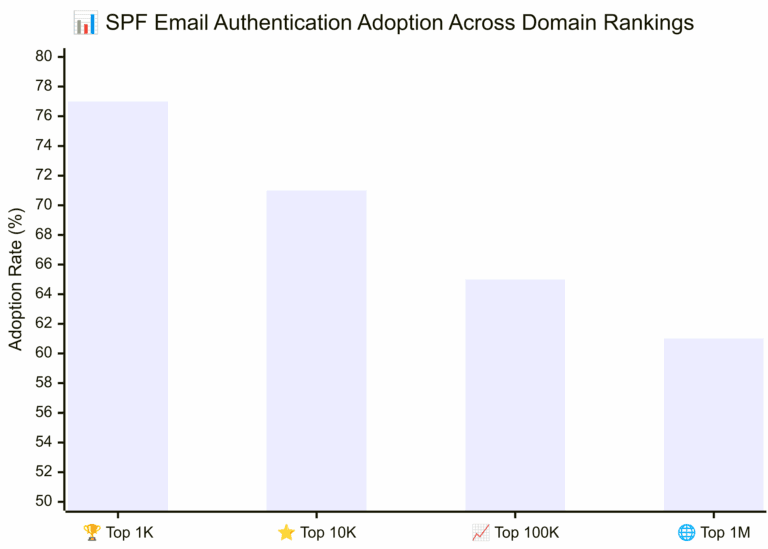
39% of the top 1 million domains lacked an SPF record, leaving them vulnerable to spoofing attacks. Even more concerning, domains not used for emailing should have a simple v=spf1 -all SPF record, clearly indicating that no IP address is authorized to send emails on their behalf to prevent domain hijacking.
DKIM (DomainKeys Identified Mail): Ensuring Message Integrity

How DKIM Works
DKIM (DomainKeys Identified Mail) functions like a tamper-evident seal on your emails, ensuring that messages haven’t been altered during transit from sender to recipient. Think of it as a sophisticated digital wax seal that proves both authenticity and integrity. When you send an email, your mail server creates a unique cryptographic fingerprint (hash) of specific parts of the email content, including headers and body text. This fingerprint is then encrypted using your domain’s private key, creating a digital signature that gets attached to the email header. The receiving server can then use your public key (published in your DNS records) to decrypt this signature and verify that the email content matches the original fingerprint. If even a single character has been changed during transmission, the verification will fail, alerting the recipient that the email may have been tampered with.
DKIM adds a cryptographic signature to your emails using public-key cryptography. The sending server signs the email with a private key, while the public key is published in DNS for verification.
Technical Process
- Sending server generates cryptographic hash of email content
- Hash is encrypted with domain’s private key
- Signature is added to email header as DKIM-Signature
- Receiving server retrieves public key from DNS
- Decrypts signature and compares with computed hash
Sample DKIM DNS Record
selector1._domainkey.yourdomain.com TXT “v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC…”
Record Breakdown
- selector1._domainkey – DKIM selector and subdomain structure
- v=DKIM1 – DKIM version
- k=rsa – Key type (RSA encryption)
- p= – Public key data (base64 encoded)
DKIM Growth Trends
DKIM Adoption Growth (.fr Domains)
35% │ ████████████████████████████████████
30% │ ██████████████████████████████████ (33.0% – 2024)
25% │ ███████████████████████████████
20% │ ████████████████████████ (23.1% – 2023)
15% │ ████████████████████
10% │ ██████████████
5% │ ███████
0% └────────────────────────────────────
2023 2024
The proportion for which we inferred the deployment of DKIM went from 23.1% in 2023 to 33.0% in 2024 in France’s .fr domain analysis, indicating growing awareness of DKIM’s importance.
DMARC (Domain-based Message Authentication, Reporting & Conformance): The Policy Enforcer
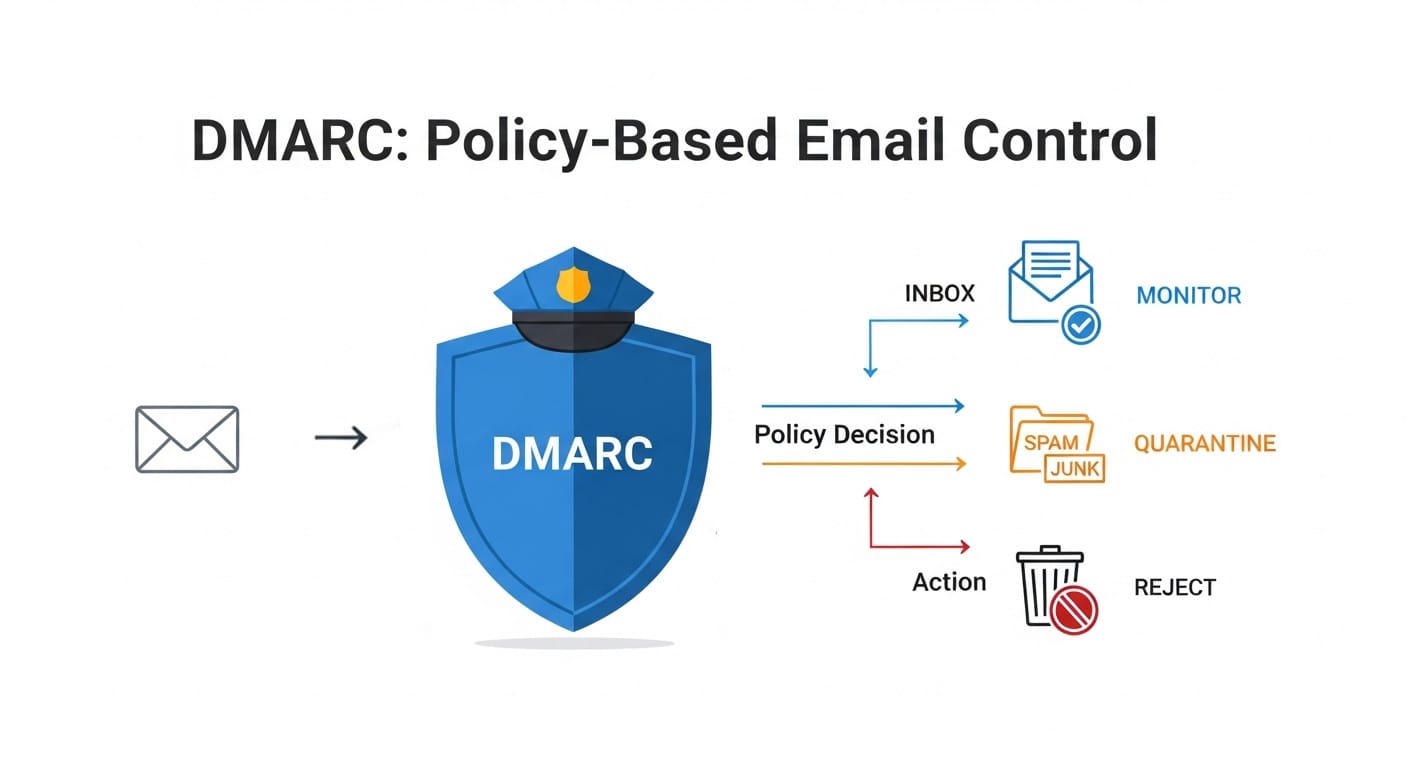
How DMARC Works
DMARC builds upon SPF and DKIM by allowing domain owners to specify how receiving mail servers should handle emails that fail authentication. It performs alignment checks to ensure the visible “From” domain matches the authenticated domain.
Technical Process
- Check SPF authentication and alignment
- Check DKIM authentication and alignment
- Apply DMARC policy if both SPF and DKIM fail
- Send aggregate reports to specified addresses
- Generate forensic reports for failed messages (if requested)
Sample DMARC DNS Record
_dmarc.yourdomain.com TXT “v=DMARC1; p=reject; pct=100; rua=mailto:dmarc@yourdomain.com; ruf=mailto:forensic@yourdomain.com; sp=reject; adkim=s; aspf=s”
Record Breakdown
- v=DMARC1 – DMARC version
- p=reject – Policy for main domain (none/quarantine/reject)
- pct=100 – Percentage of emails to apply policy to
- rua= – Email address for aggregate reports
- ruf= – Email address for forensic reports
- sp=reject – Policy for subdomains
- adkim=s – DKIM alignment mode (strict)
- aspf=s – SPF alignment mode (strict)
DMARC Policy Distribution
DMARC Policy Usage (Top 1M Domains with DMARC)
┌─────────────┬─────────────┬─────────────┐
│ Policy │ Count │ Percentage │
├─────────────┼─────────────┼─────────────┤
│ p=none │ 190,988 │ 57.2% │
│ p=quarantine│ 76,394 │ 22.9% │
│ p=reject │ 66,618 │ 19.9% │
└─────────────┴─────────────┴─────────────┘
Despite its critical importance, DMARC adoption among the top 1 million websites remains relatively low, with only about one-third (33.4%) of the domains having a valid DMARC record in place. More troubling, 57.2% employ a DMARC policy of none (p=none), indicating that emails failing the DMARC verification will be delivered as usual, effectively rendering the protection useless.
However, change is accelerating. 53.8% of senders told us they were using DMARC in 2024, representing an 11% increase from the 42.6% who’d implemented DMARC in 2023.
BIMI (Brand Indicators for Message Identification): The Visual Trust Signal

How BIMI Works
BIMI allows brands with properly configured DMARC (at p=quarantine or p=reject) to display their verified logos next to emails in recipients’ inboxes. It requires either a Verified Mark Certificate (VMC) or Common Mark Certificate (CMC).
Technical Process
- Email passes DMARC authentication
- Receiving server checks for BIMI record in DNS
- Retrieves brand logo from specified URL
- Validates certificate (VMC/CMC) if present
- Displays logo in email client interface
Sample BIMI DNS Record
default._bimi.yourdomain.com TXT “v=BIMI1; l=https://yourdomain.com/logo.svg; a=https://yourdomain.com/certificate.pem”
Record Breakdown
- default._bimi – BIMI selector and subdomain
- v=BIMI1 – BIMI version
- l= – URL to SVG logo file (square format, specific requirements)
- a= – URL to authority evidence (VMC/CMC certificate)
BIMI Adoption Trends
BIMI Implementation Growth (Top 1M Domains)
12,000 │
10,000 │ ████████████ (9,661 – Jan 2025)
8,000 │ ████████████
6,000 │ ████████████ (7,562 – May 2024)
4,000 │ ████████████
2,000 │ ████████████
0 └────────────────────────────────
May 2024 Jan 2025
Error Rate: 41.8% (2024) → 53.6% (2025)
The number of domains with BIMI DNS records increased by 28%, from 7,562 domains in May 2024 to 9,661 domains in January 2025. However, implementation quality remains a challenge, as the number of BIMI-enabled domains with one or more errors also grew significantly by 64%.
Common BIMI Implementation Issues
- SVG Compliance: Non-compliant SVG files continue to dominate as the most common error, with nearly the same percentage across 2024 (28.4%) and 2025 (27.5%)
- Certificate Problems: Invalid or expired Verified Mark Certificates
- DMARC Prerequisites: Insufficient DMARC enforcement (must be p=quarantine or p=reject)
The Business Case: Why Implementation Matters

Enhanced Email Deliverability
Major email providers have raised the stakes significantly. Starting in 2024, all senders must be using some form of email authentication. If you are a bulk sender – which generally means sending thousands of emails every day – then you need to be using all three of these authentication methods.
The impact is measurable: 65% reduction in unauthenticated messages sent to Gmail users, 50% more bulk senders started following best security practices, and 265 billion fewer unauthenticated messages were sent in 2024.
Brand Protection and Trust
Email authentication directly protects your brand from impersonation. BIMI gives brands an opportunity to reinforce their logo while building trust as a sender of authentic messages, while DMARC prevents cybercriminals from sending fraudulent emails that appear to come from your domain.
Regulatory Compliance
The regulatory landscape is shifting rapidly. The Payment Card Industry Data Security Standard (PCI DSS) has introduced new requirements in its 4.0 update, effective March 2025, that mandate the implementation of anti-phishing mechanisms like DMARC, SPF, and DKIM. This affects any business that processes credit card payments.
Additionally, organizations processing payment cards must implement DMARC email authentication by March 31, 2025, facing penalties for non-compliance under PCI DSS v4.0.
Global Adoption Trends: A Mixed Picture
The adoption landscape varies significantly across regions and industries. Looking at all domains, including those that do not publish an MX record at the apex, we find that 66.2% publish an SPF policy, 28.5% seem to have deployed DKIM and 15.1% publish a DMARC policy in France, showing substantial room for improvement.
Encouragingly, more than 75% of respondents sending over 50,000 emails per month are confident they use both SPF and DKIM protocols, indicating that high-volume senders are taking authentication seriously.
The Cost of Inaction: When Things Go Wrong
The consequences of poor email authentication configuration extend far beyond technical glitches. Nearly 30% of BEC claims involved funds transfer fraud (FTF). These claims had an average initial loss amount of $185,000.
Organizations without proper authentication face multiple risks:
Deliverability Issues
Bulk email senders would be now required to keep their spam rate threshold below 0.3%. If a sender exceeds this threshold, it might negatively impact their email infrastructure.
Security Vulnerabilities
Even organizations with fewer than 1,000 employees have a 70% weekly probability of experiencing at least one BEC attack.
Reputation Damage
When cybercriminals successfully impersonate your domain, it doesn’t just harm your immediate targets—it damages your brand’s trustworthiness permanently.
Financial Losses
The average cost per spoofed email incident is $4.88 million.
Implementation Challenges and Solutions
While the benefits are clear, implementation isn’t without challenges. While BIMI adoption has grown by 28%, the accompanying 64% increase in domains with errors highlights a critical gap between adoption and proper implementation.
Common implementation issues include:
- Misconfigured DNS Records: Incorrect SPF or DKIM records can cause legitimate emails to fail authentication
- Incomplete Domain Coverage: Many organizations forget to protect subdomains used for email
- Policy Misalignment: Setting DMARC to “none” provides visibility but no protection
- Vendor Management: Failing to account for all third-party services that send email on your behalf
The Road Ahead: Preparing for 2025 and Beyond
The email authentication landscape is rapidly evolving, with several key trends shaping the future:
Stricter Enforcement
With more ISPs expected to follow Yahoo and Google, the push for stricter email authentication measures is set to grow in 2025.
BIMI Expansion
In 2024, Gmail expanded BIMI adoption by supporting Common Mark Certificates, making it easier for marketers to implement BIMI without obtaining a trademarked logo.
Industry Standardization
PCI DSS (Payment Card Industry Data Security Standard), a set of rules aimed at protecting financial data. Version 4.0 of the PCI DSS standard will make it obligatory for SPF, DKIM and DMARC to be put in place with effect from 1 April 2025.
Best Practices for Implementation
Based on current industry standards and emerging requirements, organizations should:
- Start with SPF and DKIM: Establish the foundation before implementing DMARC
- Begin with DMARC p=none: Monitor authentication results before enforcing policies
- Gradually Increase Enforcement: Move from p=none to p=quarantine to p=reject over time
- Monitor Continuously: Use DMARC reports to identify and address authentication failures
- Plan for BIMI: Once DMARC is at p=quarantine or p=reject, consider implementing BIMI for brand visibility
Conclusion: The Time to Act is Now
Email authentication is no longer a technical nicety—it’s a business imperative. With 963,994 phishing attacks in Q1 2024 and mounting regulatory pressure, organizations cannot afford to delay implementation.
The message from major email providers is clear: authenticate or be blocked. The choice facing businesses today isn’t whether to implement email authentication, but how quickly they can do it properly. Those who act now will not only protect their organizations from escalating cyber threats but also position themselves for success in an increasingly security-conscious digital landscape.
As we move through 2025, email authentication will separate the prepared from the vulnerable. The question isn’t whether your business can afford to implement these protections—it’s whether you can afford not to.
Citation Table
Reference | Source | Date | Link |
1 | BIMI: Updated Analysis of the Top 1 Million Domains | January 16, 2025 | |
2 | SPF, DKIM, and DMARC in 2024: Analyzing the Top 1M Domains | 2024 | https://dmarcchecker.app/articles/spf-dkim-dmarc-adoption-2024 |
3 | SPF, DKIM and DMARC: rapid rise in adoption across .fr | December 2, 2024 | |
4 | Top Stories Regarding DMARC, SPF, DKIM, BIMI, and Email Authentication | June 17, 2022 | https://dmarcreport.com/blog/top-stories-regarding-dmarc-spf-dkim-bimi-and-email-authentication/ |
5 | Email Authentication Requirements in 2025 | November 20, 2024 | https://www.mailgun.com/resources/research/email-authentication-requirements/ |
6 | Google’s 2024 DMARC Requirements: What Email Senders Need To Know | October 2, 2024 | https://expertbeacon.com/googles-2024-dmarc-requirements-what-email-senders-need-to-know/ |
7 | The State of BIMI | November 12, 2024 | |
8 | Email Authentication Protocols in 2024: SPF, DKIM, DMARC & BIMI | February 19, 2025 | https://www.emailonacid.com/blog/article/email-deliverability/email-authentication-protocols/ |
9 | What’s Next For Email Marketing – Trends Shaping 2025 | May 21, 2025 | https://www.data-axle.com/resources/blog/whats-next-email-marketing/ |
10 | FAQs For Marketers & ESPs – BIMI Group | October 10, 2024 | |
11 | A Look at U.S. Business Email Compromise Statistics (2024) | March 28, 2024 | https://www.thesslstore.com/blog/business-email-compromise-statistics/ |
12 | February 1, 2024: A new era of email authentication begins | May 7, 2024 | https://blog.redsift.com/email/february-1-2024-a-new-era-of-email-authentication-begins/ |
13 | Insurer Coalition: Costs From Business Email Compromise Rise in 2024 | May 13, 2025 | https://www.insurancejournal.com/news/national/2025/05/12/823055.htm |
14 | Deprecation of Basic authentication in Exchange Online | Microsoft Learn | |
15 | Google and Yahoo’s New Email Authentication Policy for 2024 | November 27, 2023 | https://dmarcreport.com/blog/google-and-yahoos-new-email-authentication-policy-for-2024/ |
16 | Business Email Compromise Costs $55bn Over a Decade | September 12, 2024 | https://www.infosecurity-magazine.com/news/business-email-compromise-55bn/ |
17 | The steps I have taken for the email authentication changes in February 2024 | January 25, 2024 | https://thewebsitementor.com/email-authentication-changes-in-february-2024/ |
18 | Business Email Compromise Statistics 2025 (+Prevention Guide) | 2024 | https://hoxhunt.com/blog/business-email-compromise-statistics |
19 | Exchange Online to retire Basic auth for Client Submission (SMTP AUTH) | June 12, 2025 | |
20 | A complete guide to email compliance requirements | May 20, 2025 | |
21 | Anti-phishing mechanisms such as DMARC, SPF, and DKIM to become a requirement for PCI DSS 4.0 | August 27, 2024 | |
22 | Implementing DMARC to Meet PCI DSS V4.0 Requirements | September 8, 2023 | |
23 | DMARC For PCI DSS 4.0: Strengthening Email Security For Compliance | April 1, 2025 | |
24 | DMARC for PCI DSS: Your Practical Guide to 2025 Compliance Implementation | March 24, 2025 | |
25 | Credit Card Industry Spurs Businesses to Use DMARC Tools | 2024 | https://www.mimecast.com/blog/credit-card-industry-spurs-businesses-to-use-dmarc-tools/ |
26 | DMARC enforcement will soon be required as part of PCI SCC 4.0 | September 24, 2024 | https://www.valimail.com/blog/dmarc-enforcement-will-soon-be-required-as-part-of-pci-scc-4-0/ |
27 | Payment Card Industry Recommends DMARC, DKIM, SPF | March 11, 2025 | |
28 | DMARC PCI DSS: Now a mandatory requirement for version 4.0 | July 14, 2023 | https://securityboulevard.com/2023/07/dmarc-pci-dss-now-a-mandatory-requirement-for-version-4-0/ |
29 | SPF, DKIM & DMARC Setup Guide: Complete Email Security 2025 | June 17, 2025 | https://www.ucartz.com/blog/email-security-spf-dkim-dmarc-complete-guide/ |
30 | DMARC Requirements for PCI DSS 4.0: Everything You Need to Know | August 29, 2023 | https://www.linkedin.com/pulse/dmarc-requirements-pci-dss-40-everything-you-need-know-shanmugam |